The digital world, for all its convenience, comes with a stark reality: your personal data is a valuable commodity. From the moment you wake up and check your phone to the time you settle in to stream your favorite show, a complex web of trackers, advertisers, and data brokers is working behind the scenes. In 2025, with AI-driven surveillance and data breaches becoming more sophisticated, using reliable online privacy software, trusted privacy apps, or secure digital tools is no longer a niche concern—it’s a fundamental necessity.
What is Online Privacy Software?
Online privacy software encompasses a wide range of tools and applications designed to protect a user’s digital identity and personal information from unauthorized access, tracking, and surveillance. These online privacy software solutions work by creating a protective layer between you and the internet, obfuscating your location, encrypting your data, and blocking unwanted trackers. The goal is to make your online activity anonymous, secure, and private, giving you full control over your information.
In 2025, the landscape of digital privacy is evolving rapidly. The rise of generative AI has led to more complex phishing schemes and data analysis, making it easier for bad actors to profile individuals. With these risks growing, online privacy software, privacy protection tools, and secure browsing apps are becoming essential parts of everyday life.
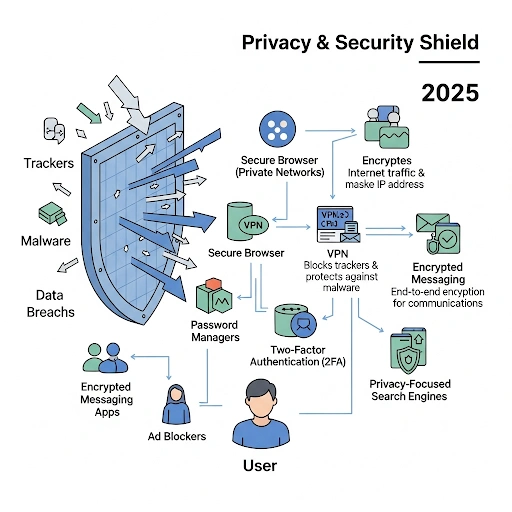
Why It Matters: The Benefits of Using Internet Safety Tools
Adopting online privacy software offers a multitude of benefits that go far beyond simply hiding your browsing history. With trusted privacy software, secure online tools, and reliable privacy apps, you gain stronger protection against data theft and unwanted tracking. Using well-designed privacy software solutions also helps maintain digital freedom while keeping personal information safe.
- Protection from Data Brokers: Data brokers collect and sell your personal information—including your purchasing habits, social media activity, and even medical history—to advertisers and other companies. Privacy tools make it much harder for these brokers to build a detailed profile of you, ensuring your data remains your own.
- Defense Against Malicious Attacks: Phishing, ransomware, and other forms of malware often exploit vulnerabilities in an unprotected connection. Tools like VPNs and secure browsers encrypt your data, making it unreadable to hackers who might try to intercept it on public Wi-Fi networks.
- Circumventing Censorship and Geographic Restrictions: For those living in countries with strict internet censorship, or for users who want to access content unavailable in their region, privacy tools provide a way to bypass these restrictions. They allow you to virtually “relocate” your device, granting you access to a free and open internet.
- Preventing Ad and Website Tracking: Every website you visit and every ad you click is a potential data point for trackers. Privacy browsers and extensions block these trackers, reducing the number of targeted ads you see and preventing companies from building a comprehensive profile of your online behavior.
- Maintaining Anonymity: In an age where everything is tied to your identity, the ability to browse the web or communicate anonymously is invaluable. This is crucial for whistleblowers, journalists, or anyone who needs to operate without revealing their identity. For a deeper dive into the importance of online anonymity, read our related article on the importance of anonymous browsing.
How Anonymous Browsing Apps and Tools Work
Understanding the core technology behind these tools is key to using them effectively. By learning how online privacy software works, exploring trusted privacy apps, and applying reliable security software, you can ensure these solutions protect you as intended. Knowing the basics of privacy software tools also helps you adapt quickly as digital threats evolve.
- VPNs (Virtual Private Networks): A VPN encrypts your internet traffic and routes it through a server operated by the VPN provider. This hides your real IP address and location, making it appear as though your connection is coming from the VPN server’s location.
- Encrypted Messaging: These apps use end-to-end encryption to ensure that only the sender and the intended recipient can read the messages. This prevents internet service providers, governments, or the app itself from intercepting and reading your private communications.
- Secure Browsers: Browsers like Tor or Brave are built with privacy as a priority. They block ads, trackers, and scripts that track your movements across the web. Tor, in particular, uses a layered encryption system that bounces your traffic through a series of volunteer-run servers, making it nearly impossible to trace.
- Password Managers: While not a privacy tool in the traditional sense, a password manager is crucial for security. It generates and stores unique, strong passwords for all your accounts, protecting you from credential stuffing attacks and making it much harder for hackers to access your personal data.
| Feature / Tool | How It Works | Use Case |
|---|---|---|
| VPN (Virtual Private Network) | Encrypts your internet traffic and hides your IP address by routing it through a remote server. | Browsing on public Wi-Fi, accessing geo-restricted content, protecting against ISP tracking. |
| Encrypted Messaging App | Uses end-to-end encryption to secure conversations, ensuring only the sender and recipient can read them. | Private conversations, sharing sensitive information, avoiding corporate or government surveillance of chats. |
| Private Search Engine | Does not track your search history, IP address, or clicks. | Searching for sensitive topics, avoiding personalized search results, maintaining privacy from search engines. |
| Ad and Tracker Blockers | Prevents third-party scripts from loading on websites, which stops tracking and targeted ads. | Reducing ad clutter, preventing data collection by advertisers, speeding up page load times. |
Real-Life Use Case: The Digital Nomad’s Privacy Stack
Meet Alex, a freelance writer and digital nomad who travels the world. For Alex, a robust privacy setup isn’t just a preference—it’s a business necessity. By combining online privacy software, secure browsing tools, and trusted digital security apps, Alex maintains a safe environment for both work and travel. Here’s a look at Alex’s personal privacy stack and how reliable privacy software solutions protect their work and personal life.
Alex starts every day by connecting to the internet using a premium VPN service. This ensures that their traffic is always encrypted, whether they’re working from a café in Bangkok or a co-working space in Berlin. Alongside the VPN, Alex relies on online privacy software and trusted security apps to keep sensitive data safe. Next, they use a secure browser like Brave, which, combined with privacy software tools and reliable online security software, automatically blocks ads and trackers, preventing advertisers from building a profile of their browsing habits. This is especially important when Alex is researching confidential topics for a client.
For communication, Alex relies on a secure communication tool like Signal for all client conversations and personal chats. Alongside online privacy software, Alex builds extra layers of protection to keep sensitive data safe. Using online privacy software also gives peace of mind knowing that messages are end-to-end encrypted and can’t be read by anyone else. For files, they rely on online privacy software to support encrypted cloud storage and keep information secure.
Common Mistakes to Avoid with Your Privacy Tools
Even with the best tools, a few common pitfalls can undermine your efforts. Relying only on online privacy software without proper updates can weaken your defenses. Ignoring how online privacy software integrates with other systems may also reduce its effectiveness. Balancing online privacy software with consistent good habits ensures stronger and more reliable protection.
- Assuming a “One-and-Done” Approach: No single tool will protect you from all threats. Using a VPN without a secure browser, or an encrypted messaging app without a password manager, leaves significant vulnerabilities. The key is to build a comprehensive privacy ecosystem.
- Using Free VPNs: Many free VPN services make money by logging and selling user data—the very thing you’re trying to prevent. While they can be tempting, they often pose a greater privacy risk than no VPN at all. It’s almost always better to invest in a reputable, no-log paid service.
- Ignoring Updates: Software vulnerabilities are constantly being discovered and patched. Failing to update your privacy tools, operating system, and apps leaves you exposed to new threats.
- Overlooking the “Human Factor”: The biggest threat to your privacy is often human error. Sharing too much information on social media, using weak passwords, or clicking on suspicious links can bypass even the most advanced technical safeguards.
Expert Tips and Best Practices
To get the most out of your privacy tools, consider these expert-level tips. Using online privacy software effectively means knowing how it fits into your daily routine. Regularly updating online privacy software ensures it works at its best, while combining different layers of online privacy software helps build stronger protection and long-term security.
- Audit Your Digital Footprint: Start by using a free online tool to see what information about you is publicly available. This can be an eye-opening exercise and will help you prioritize what needs to be protected.
- Diversify Your Accounts: Create unique, strong passwords for every online account. Use a password manager to store them securely so you don’t have to remember them.
- Use Multi-Factor Authentication (MFA): Enable MFA on every account that supports it. This adds a crucial second layer of security, making it much harder for a hacker to gain access even if they have your password.
- Be Smart About Social Media: Be mindful of what you post. Avoid sharing personal details like your location, phone number, or travel plans. Review your privacy settings on platforms like Facebook and Instagram regularly.
- Don’t Overlook Metadata: Photos, documents, and other files often contain hidden metadata that can reveal information about you, such as your location, the device you used, and the date the file was created. Use tools to scrub this metadata before sharing files publicly.
FAQ Section
- Q: Are VPNs legal?A: Yes, in most countries, VPNs are completely legal. However, some countries with strict internet censorship have banned or restricted their use. It’s important to check the laws of your specific location.
- Q: Do I need a VPN for my phone as well as my computer?A: Yes. Your phone connects to the internet through both Wi-Fi and cellular data, and both connections are vulnerable to tracking and surveillance. Using a VPN on your phone is just as important as using one on your computer.
- Q: What is the difference between a VPN and a proxy server?A: A proxy server only reroutes your traffic, but it doesn’t encrypt it. A VPN both reroutes and encrypts your traffic, providing a much higher level of security and privacy.
- Q: Can I really be anonymous online?A: Achieving complete anonymity online is extremely difficult. The goal of privacy tools is to make you as anonymous as possible and to significantly raise the bar for anyone trying to track you.
- Q: What is a “zero-log” policy?A: A zero-log policy means that the privacy tool provider does not keep any records of your activity, including your browsing history, IP address, or connection timestamps. This is a crucial feature to look for when choosing a provider.
- Q: How do secure communication tools work?A: These tools use end-to-end encryption, which scrambles your messages on your device before they are sent and unscrambles them only on the recipient’s device. The messages are unreadable by anyone in between, including the app provider.
- Q: Is it safe to use a public Wi-Fi network?A: Without proper protection, public Wi-Fi is highly unsafe. Hackers can easily intercept your data and steal sensitive information. Using a VPN is the minimum requirement for safe browsing on a public network.
Conclusion
The digital landscape is a challenging one, but with the right online privacy software in your toolkit, you can navigate it with confidence. From understanding the basics of online privacy software to implementing an advanced privacy stack, you have the power to protect your data. By choosing reputable online privacy software and adopting smart digital habits, you can stop being a product and start reclaiming your privacy.
For more helpful guides on internet safety, check out our comprehensive guide to online security and explore the vast resources at PrivacyTools.io.
